Since you are here, I assume you are done with the Basics Of Computer Networks. To have an overall idea on this topic, in this article, we will explore and learn about Network Models, Protocols and Organizations that create these Protocols.
So, what are protocols exactly? Let's find out.
Communication Protocols and Standards
Imagine communication protocols as the rules and guidelines that devices follow to talk and understand each other. Just like people need a shared language and etiquette to have a meaningful conversation, devices, too, need protocols to exchange information in a clear and organized way. These protocols ensure that when you send a message or a request, the receiving device knows how to interpret it correctly. They establish a common ground for devices to communicate coherently, ensuring that data arrives where it should and is understood without confusion.
OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a computing system into seven layers. Each layer serves a specific purpose and interacts with the layers above and below it. The model was developed by the International Organization for Standardization (ISO) to facilitate communication between different systems and vendors. Let's dive deep into each layer.
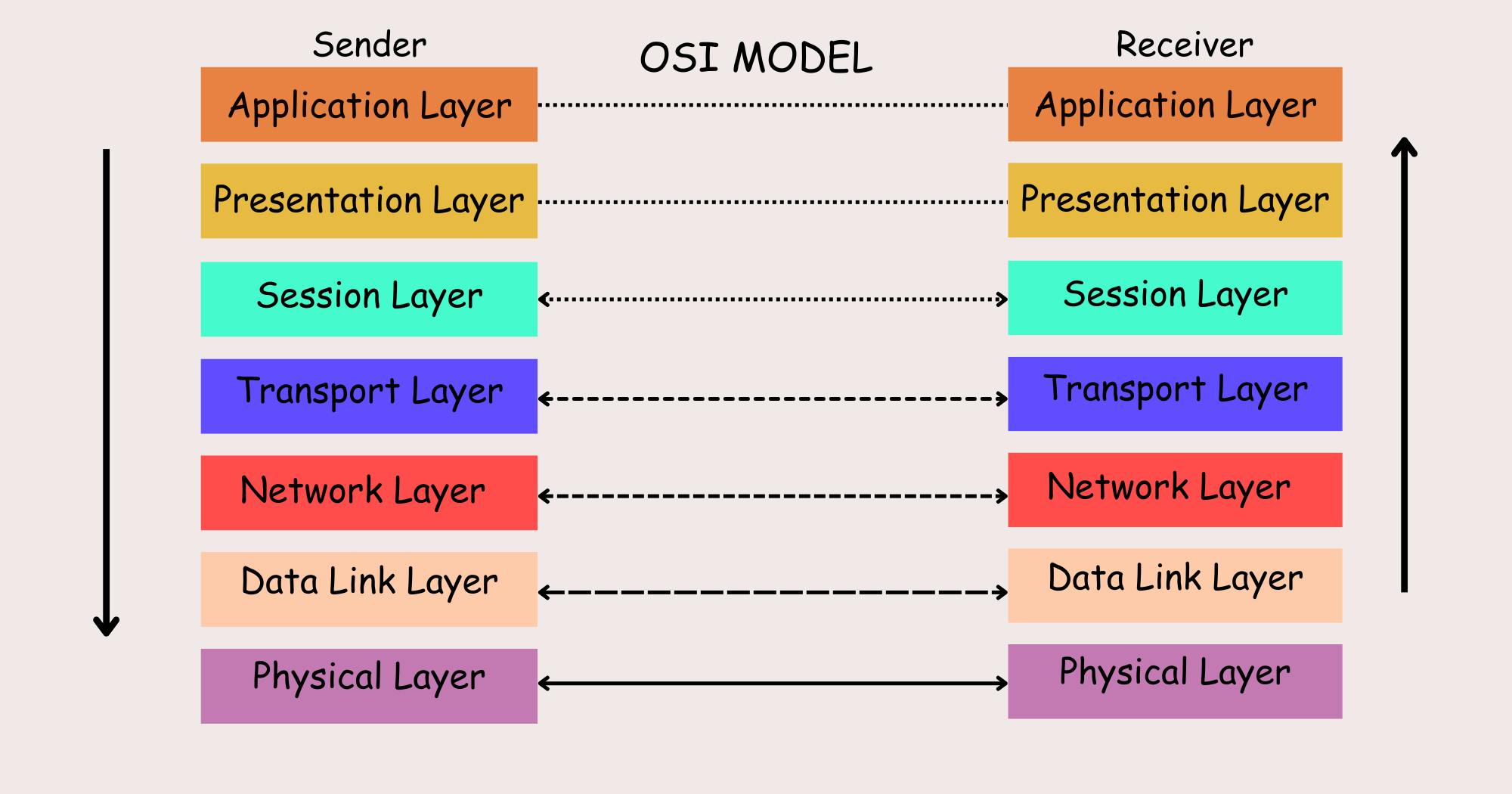
Physical Layer:
It defines the hardware characteristics, such as cables, connectors, voltage levels, and physical transmission mediums.
This layer deals with signals and bit synchronization.
Examples of physical layer technologies include Ethernet cables, fiber optics, and wireless transmission.
Data Link Layer:
This layer is divided into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC).
The LLC sublayer handles flow control, error checking, and synchronization at the logical level.
The MAC sublayer deals with the addressing of frames and access to the physical medium.
Network Layer:
IP (Internet Protocol) operates at this layer and is responsible for logical addressing (IPv4 or IPv6).
Routing is a primary function where routers make decisions about the best path for packets to reach their destination.
Transport Layer:
The two primary transport layer protocols are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
TCP provides reliable, connection-oriented communication with features like flow control, error correction, and retransmission of lost data.
UDP is connectionless and provides faster but less reliable communication.
Session Layer:
This layer manages sessions or connections between applications. It establishes, maintains, and terminates dialogues or connections.
Functions include dialogue control, synchronization, and managing tokens for token-passing systems.
Presentation Layer:
Responsible for translating data between the application layer and the lower layers. It ensures that data is presented in a format that the application layer can understand.
Encryption and compression of data happen at this layer, ensuring secure and efficient communication.
Application Layer:
The topmost layer that directly interacts with end-user applications.
It provides network services directly to end-users and application processes, including file transfers, email, and remote file access.
Protocols at this layer are specific to application requirements, such as HTTP for web browsing, FTP for file transfers, and SMTP for email communication.
Each layer plays a distinct role in the communication process, and a problem at one layer can be diagnosed and resolved independently of the other layers. OSI Model is not an actual adapted network model but is used as a blueprint to build new network models and protocols. For example the TCP/IP Protocol Suite.
TCP/IP Protocol Suite
The TCP/IP (Transmission Control Protocol/Internet Protocol) model is another networking model that merges the top 3 layers of the OSI Model into one layer and the last two into one layer. Thus, has four layers. This is an actual practical model.
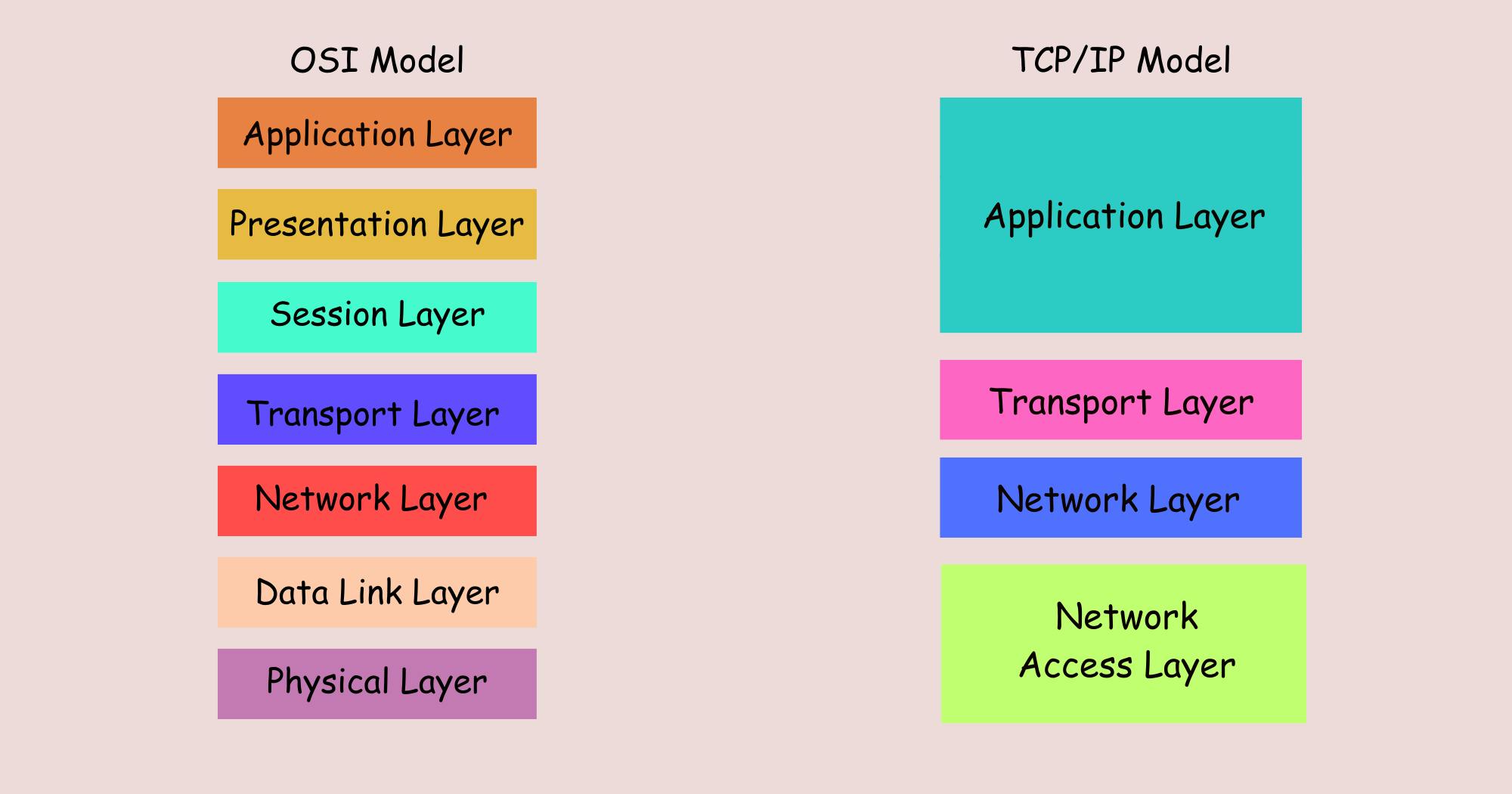
Network Access Layer:
This layer is the combination of the OSI model's Physical and Data Link layers.
It manages the physical connection to the network and the framing of packets.
MAC (Media Access Control) addressing, error detection, and basic error correction are done in this layer.
Examples of technologies operating at this layer include Ethernet, Wi-Fi (IEEE 802.11), and PPP (Point-to-Point Protocol).
Network Layer:
Corresponds to the OSI Network Layer.
Core protocols at this layer include IP (Internet Protocol), ICMP (Internet Control Message Protocol), and routing protocols (e.g., OSPF - Open Shortest Path First).
IP is responsible for logical addressing and packet forwarding between different networks.
ICMP handles error reporting and diagnostic functions.
Transport Layer:
This layer is equivalent to the OSI Transport Layer.
Primarily uses two protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
Ports are used to distinguish different services or applications on a single device.
Application Layer:
This layer is the combination of Application, Session and Presentation layers of the OSI Model.
Application-specific protocols and services are carried out in this layer.
Examples of application layer protocols include HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and DNS (Domain Name System).
This layer is where applications communicate and exchange data.
The TCP/IP model is often used as a practical and simplified guide for networking, and it's more closely aligned with real-world Internet protocols. Many networking professionals and system administrators use the TCP/IP model for troubleshooting and configuring network devices.
Important Protocols
HTTP/HTTPS (Hypertext Transfer Protocol/Secure):
Used for communication between services, APIs, and web applications. Critical for integrating and automating various tools.
SSH (Secure Shell):
Enables secure access to servers for configuration management, deploying applications, and running commands remotely.
SMTP (Simple Mail Transfer Protocol):
Sends email notifications for alerts, status updates, and communication within the team.
SNMP (Simple Network Management Protocol):
Monitors and manages network devices, providing insights into performance and health.
DNS (Domain Name System):
Automates domain management for applications, directing traffic to the correct servers. DNS is like an internet phonebook. It translates easy-to-remember website names (like google.com) into IP addresses that devices understand. This helps you reach websites without memorizing numbers.
LDAP (Lightweight Directory Access Protocol):
Integrates with identity management systems, enabling centralized user authentication.
TCP and UDP:
Fundamental for all network-related activities, ensuring communication between servers, services, and devices.
Wireless Protocols
Wireless protocols are communication standards that define how devices communicate wirelessly. These protocols govern the transmission of data between devices over radio frequency (RF) or infrared (IR) waves. Examples of technologies that use wireless protocols are Wi-Fi and Bluetooth.
Standards Organizations
In the world of technology, standards organizations play a crucial role in establishing rules and guidelines for various networking aspects. One of the organizations is the IEEE, which creates standards for various technological fields, including networking.
Another important organization is the IETF (Internet Engineering Task Force), which focuses specifically on developing and refining the protocols that enable the functioning of the Internet. You must have heard about ISO too right? These organizations ensure that devices and systems from different manufacturers can work harmoniously by adhering to common standards, ultimately fostering interoperability and innovation.
Conclusion
Computer networking holds immense importance in our interconnected world. It's the glue that binds our devices, allowing us to communicate, collaborate, and access information across vast distances. With networking, the global exchange of ideas and data that drives our modern society would greatly expand.
Looking ahead, networking will continue to transform. The arrival of 5G technology promises lightning-fast connections, while the Internet of Things (IoT) will expand our networked world to include everyday objects. Enhanced network security measures will protect our digital identities and information. These trends hint at a future where connectivity becomes even more seamless, making our lives smarter, safer, and more connected.
Hope you liked this one. Thank you.
